25+ network diagram that illustrates virtualization
Citrix cloud-based compliance As of January 2021 the use of Citrix Managed Azure Capacity with various Citrix DaaS editions and Workspace Premium Plus has not been evaluated for Citrix SOC 2 Type 1 or 2 ISO 27001 HIPAA or other cloud compliance requirements. Updated details in Horizon on Azure VMware Solution Architecture relative to feature enhancements for Universal Broker.
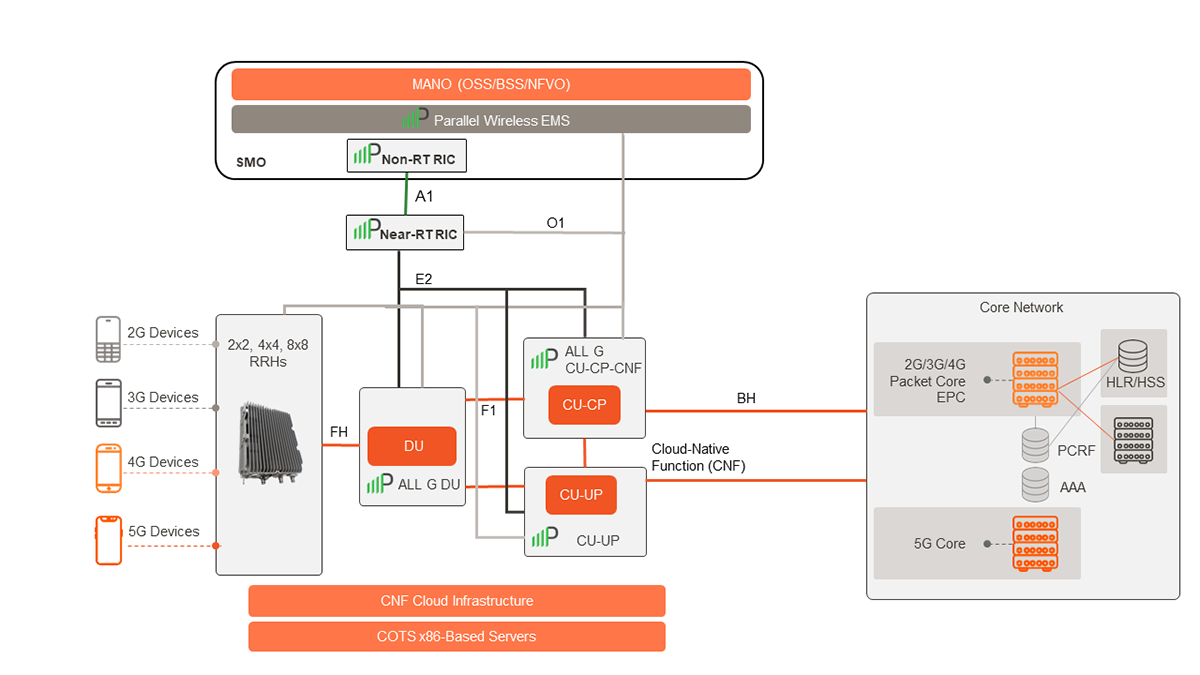
Ran Controller Parallel Wireless
To achieve the best performance out of the threat defense virtual you can make adjustments to the both the VM and the hostSee Virtualization Tuning and Optimization on Azure for more information.

. Workspace ONE Access Connector virtual appliances are hosted in the internal network. Added link in App Volumes Architecture to guide on database best practices. The worlds largest and most widely used network is the Internet.
Fixed diagram and details in the Multi-Site Design section of Horizon Cloud on Microsoft Azure Architecture. IO memory cryptography via. Receive Side ScalingThe threat defense virtual supports Receive Side Scaling RSS which is a technology utilized by.
From the perspective of the PE there is a simple point-to-point connection between an AC and an MPLS PW. A network links two or more computers to share data or resources such as a printer. Sensor used dj speaker facebook marketplace houlton maine car parts by owner craigslist 2003 dancehall riddims juniper network connect windows 10 download vba savepicture pocahontas land company lease grundig smart.
The following diagram shows the SimCLR framework. -Design update how to deploy NSX-T on VDS 7 -VSAN guidance on all the components Management and Edge consideration -EVPNBGPVRF Based Routing and lots of networking enhancements -Security and Performancefunctionality update. The sizing for OpLog is done dynamically as of.
The Inter-net is a global network of networks that uses universal standards described in Chapter 7 to connect millions of networks in more than 230 countries around. Why do guys in relationships go to bars. The foundation of the IoT Reference Model is the IoT Domain Model which introduces the main concepts of the Internet of Things like Devices IoT Services and Virtual Entities VE and it also introduces relations between these concepts.
The kernel is a computer program at the core of a computers operating system and generally has complete control over everything in the system. The abstraction level of the IoT Domain Model has been chosen in such a way that its concepts are independent of. ASR 9000 Network Virtualization nV clustering.
MINMax cluster RF2400 GiB numDevForOplog Max cluster RF225 x Remaining GiB. The network topology diagram depicts the physical or logical configuration and security posture of the various elements links nodes etc a computer enclave or network connection to DISN. Can be calculated using the following formula.
New holland 849 round baler parts diagram. Much of this knowledge had developed due to an understanding of transformers which allowed amplification and switch-like performance when built using certain materialsThe stable switching behavior. Virtual Switching System VSS on Cisco IOS switches.
And 772 on ImageNet 512 times 512 and we match BigGAN-deep even with. This design guide provides guidance and best practices for designing environments that leverage the capabilities of VMware NSX-T. The following diagram illustrates how the additional controllers and daemons communicate with Kubernetes and where the additional types are stored.
It is the portion of the operating system code that is always resident in memory and facilitates interactions between hardware and software components. 8 is a flow diagram of an example process for implementing QoS features in a multi-level arbitration structure in an on-chip interconnect. Sound and video.
It is a category of diagram that illustrates the interaction between people and organizations. A full kernel controls all hardware resources eg. Interface virtualization and fast path for network on chip US10313269B2 en 2016-12-26.
The topology diagram illustrates the System Enterprise and Information Security Architecture cited in the DoD RMF Security Plan. The following figure illustrates how load balancers distribute the load to a cluster of Workspace ONE Access appliances in the DMZ. Kalbach 2016 23.
Flow provides network segmentation and security Files provides file services and Calm provides self-service quotas and orchestration capabilities. The following diagram illustrates Citrix DaaS and its security boundaries. If you deploy the Metrics API into your cluster clients of the Kubernetes API can then query for this information and you can use.
2021 2022 emergency medicine spreadsheet. We debated how we should connect VMs to external network resources. We would like to show you a description here but the site wont allow us.
The connectors communicate to the Workspace ONE Access service nodes through the service URL using an outbound-only connection. PEs can also provide redundancy with a feature called PW. For Kubernetes the Metrics API offers a basic set of metrics to support automatic scaling and similar use cases.
The quickest way seems to introduce KubeVirt-specific code attaching a VM to a host bridge. This API makes information available about resource usage for node and pod including metrics for CPU and memory. The basic concept of using the square hysteresis loop of certain magnetic materials as a storage or switching device was known from the earliest days of computer development.
Network information processing and methods thereof Legal Events. Architectural Styles and the Design of Network-Based Software Architectures by Roy Fielding. Virtual Port Channel vPC on Cisco Nexus Switches.
Two separate data augmentation operators are sampled from the same family of augmentations t sim mathcalT and tprime sim mathcalT and applied to each data example to obtain two correlated views.

Enhanced Secure Multi Tenancy Design Guide Data Center Design Cisco Networking Computer Technology
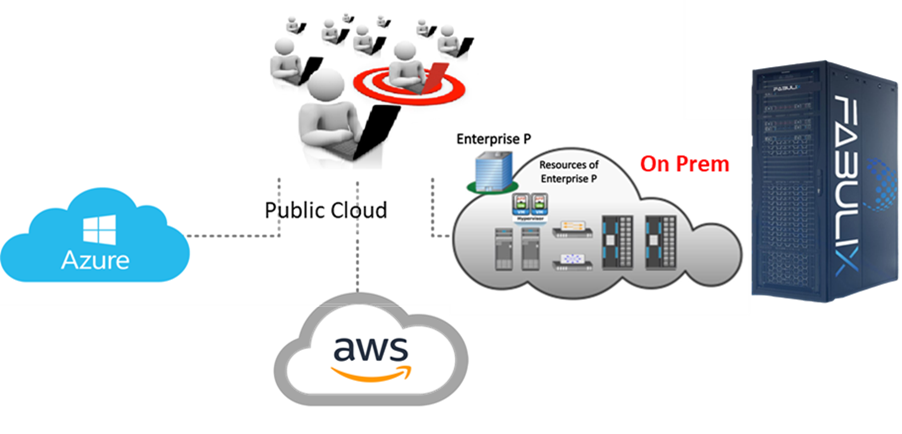
Fabulix Hci Cloudblue Catalog

Suresh Essampally Oracle Solution Architect Bloom Energy Linkedin

App V Deployment Diagram Microsoft Applications Software Architecture Diagram Visio Network Diagram
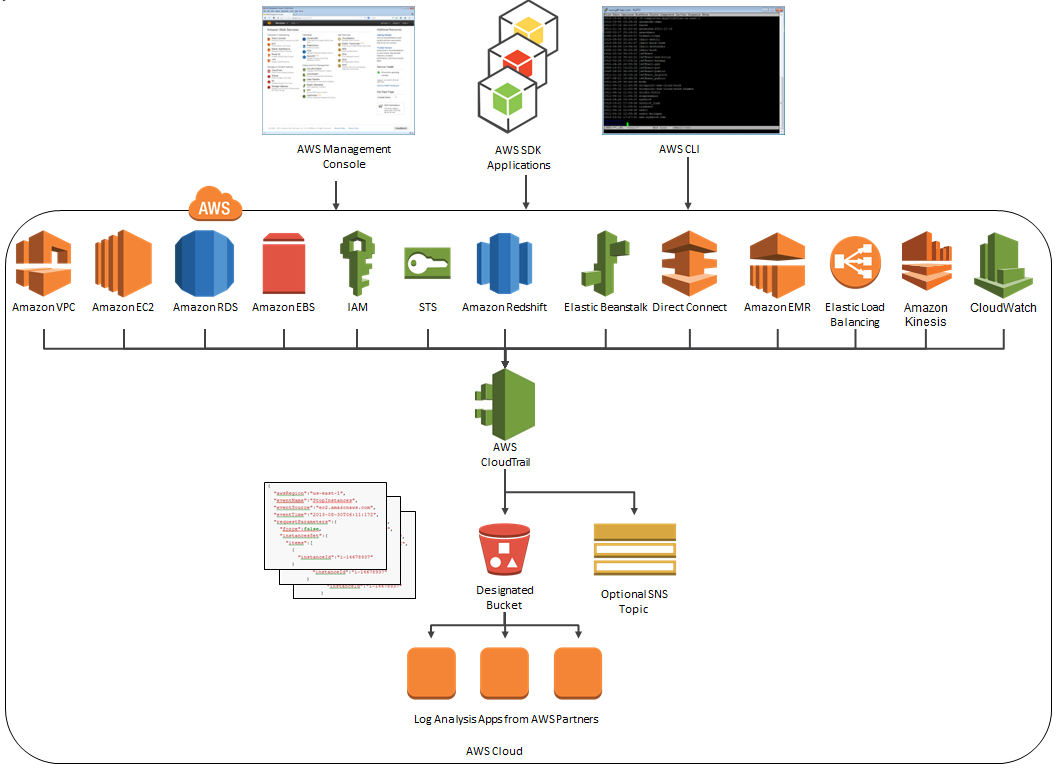
Iam Aws Blog
Docker Vs Vm Virtual Machine Key Differences You Need To Know Simplilearn
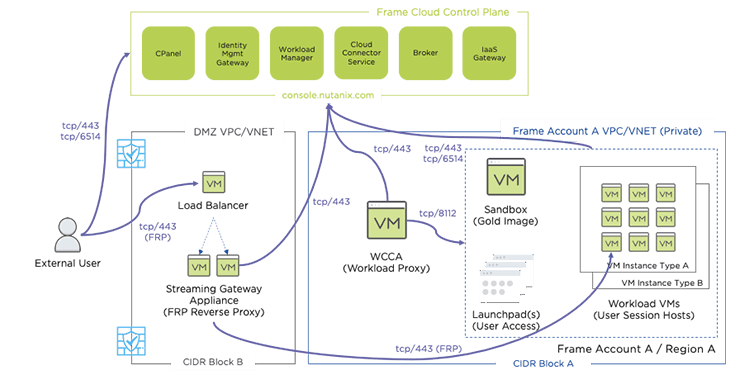
Frame Blog

Desktop Virtualization With Vmware View Managed It Services Computer Network Cloud Infrastructure

What Is Web3 And How Will It Work
2

What Is Network Virtualization Networking What Is Network Hardware Virtualization
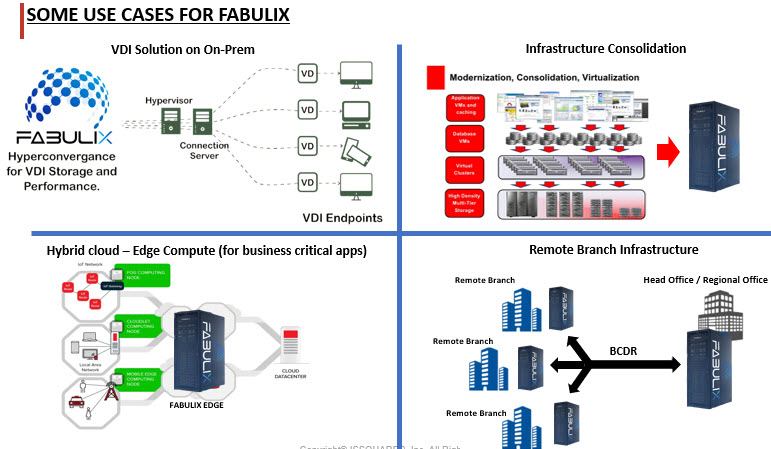
Fabulix Hci Cloudblue Catalog

Types Of Virtualization Computer Science Network Switch Storage Devices

Physical Servers Virtualization And Containers
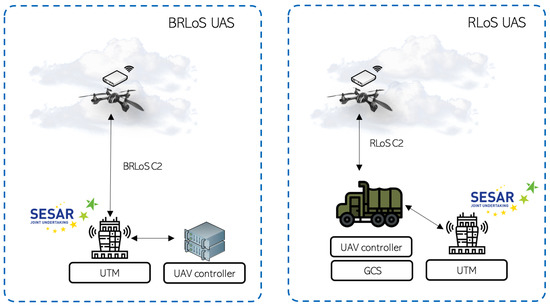
Sensors Free Full Text Cellular And Virtualization Technologies For Uavs An Experimental Perspective Html

What Is Server Virtualization Quora
What Is Server Virtualization Quora